- Harmful requests and security threats (e.g. Prompt Injections, toxic language)
- Data Privacy protection (e.g. PII leakage)
- Hallucinations
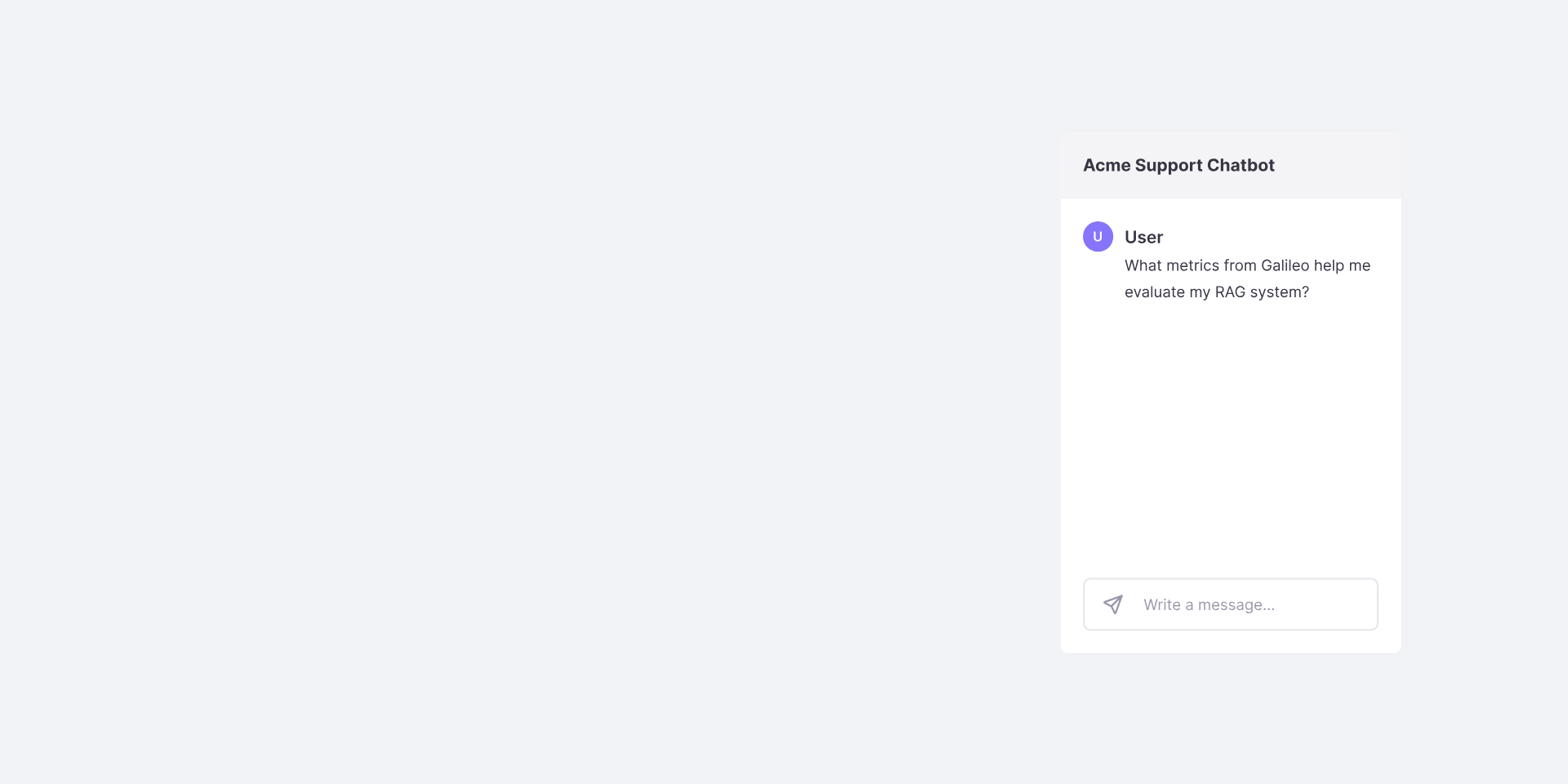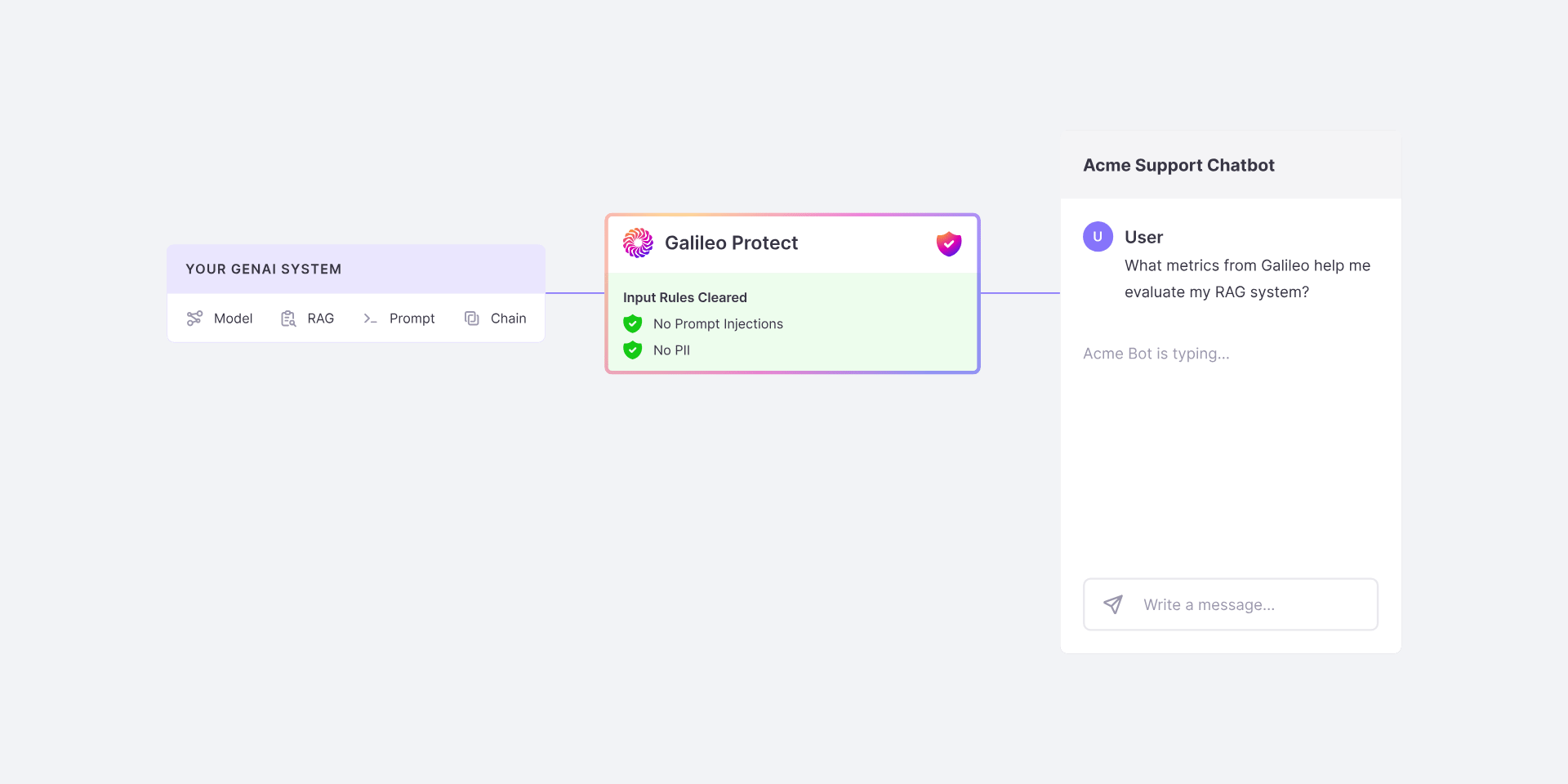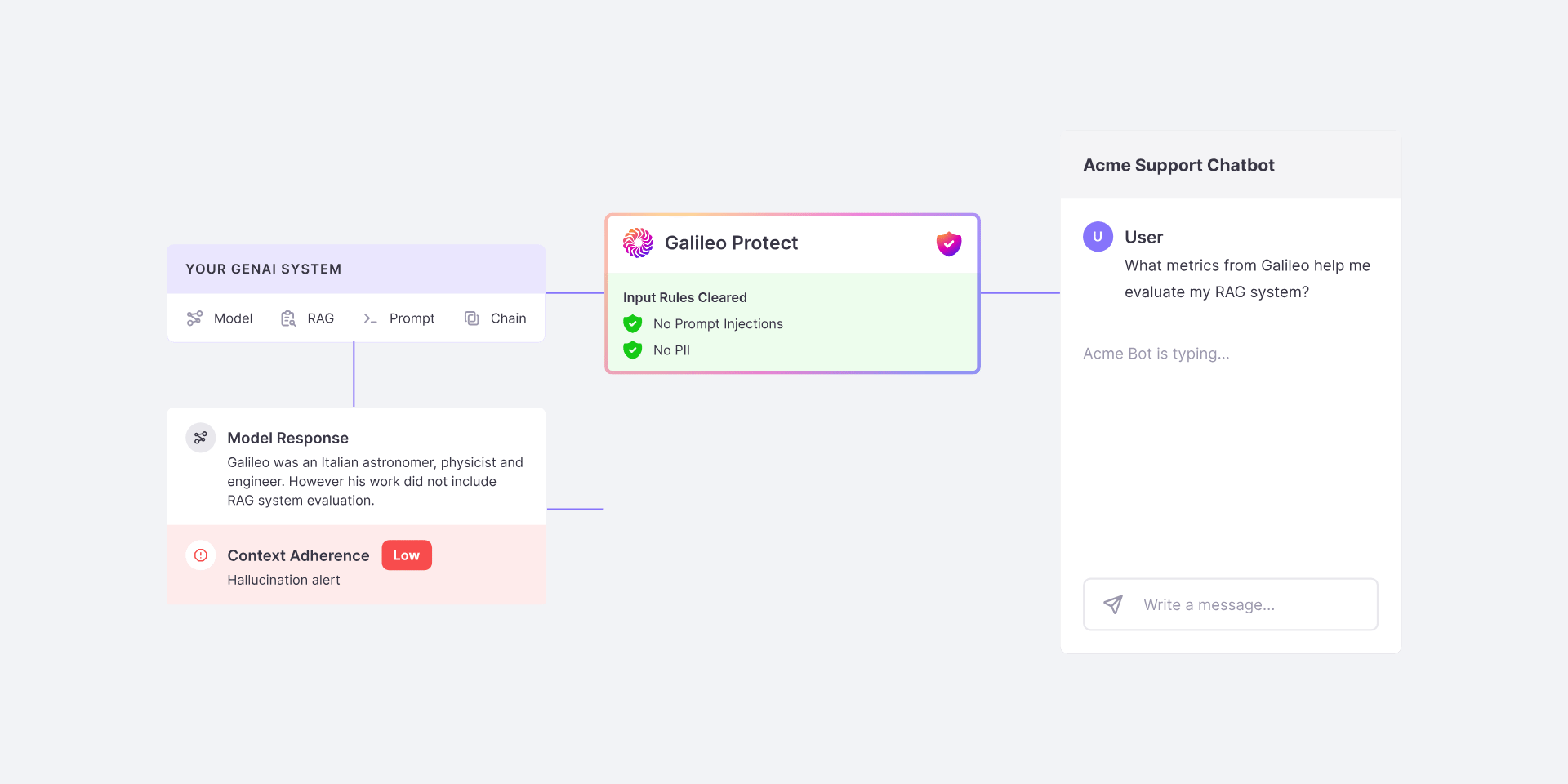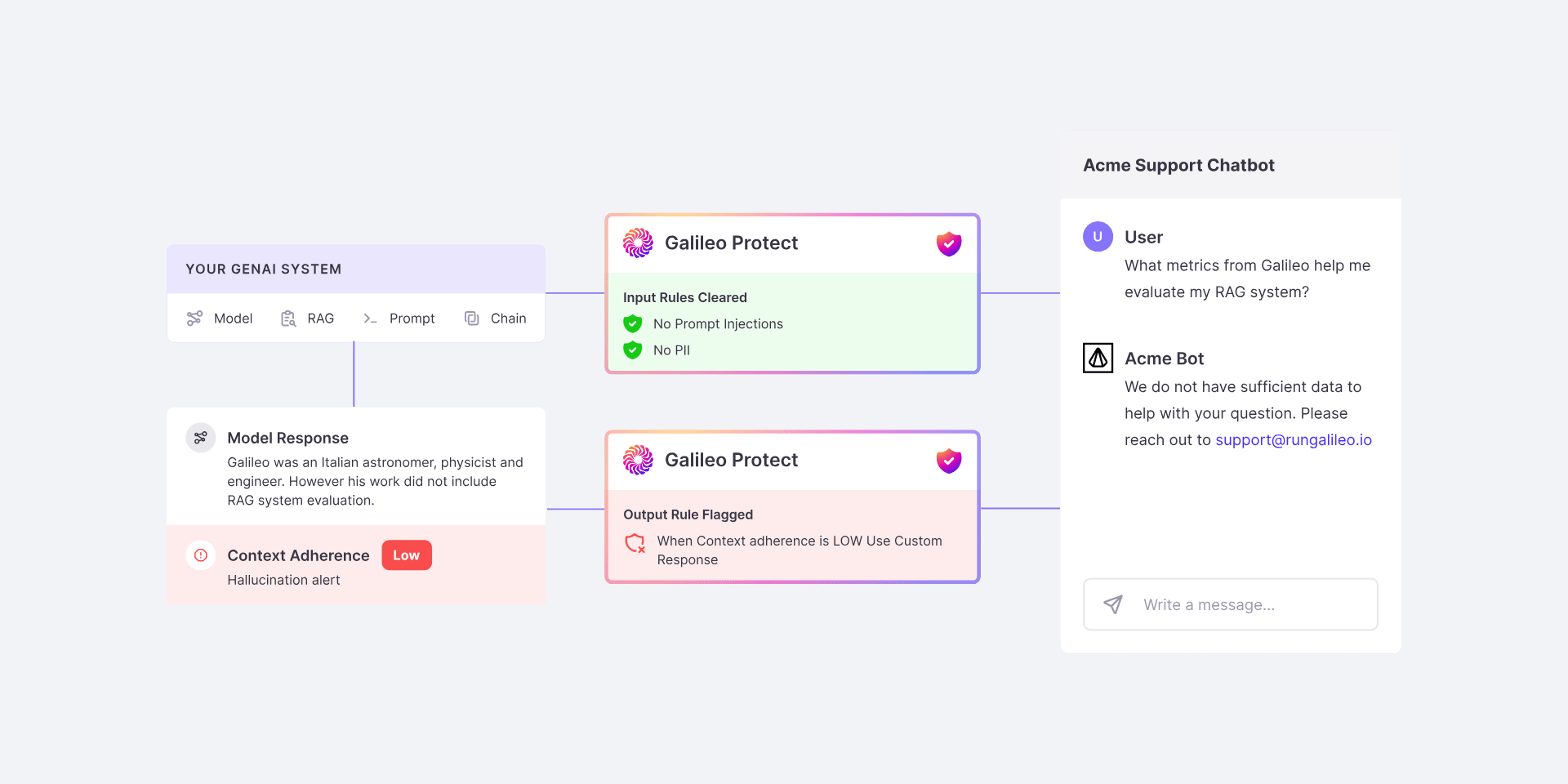
The Workflow
Establish your rules
Define you need protection from. Choose a set of metrics and conditions to
help you achieve that. Determine what your system should do when those rules are broken.
Iterate on your conditions
Run your Protect rules through a comprehensive evaluation to ensure Protect
is working for you. Run your evaluation set and check for any over- or
under-triggering. Iterate on your conditions until you’re satisfied.